Introduction
In the digital age, the legal profession has embraced technology to streamline processes, enhance client services, and improve efficiency. However, this increased reliance on digital tools also exposes law firms to cybersecurity threats and the potential compromise of sensitive data and client information. Cybersecurity in law has become a paramount concern, requiring legal professionals to adopt robust strategies and practices to safeguard their digital assets and protect the trust of their clients.
As law firms continue to integrate technology into their practices, the importance of cybersecurity cannot be overstated. These digital tools offer numerous benefits, from efficient case management to enhanced communication with clients. However, they also open the door to cyber threats like data breaches and hacking attempts. To mitigate these risks, legal professionals must not only implement state-of-the-art cybersecurity measures but also stay informed about the latest threats and best practices.
Additionally, client trust is a cornerstone of the legal profession, and safeguarding sensitive information is paramount to maintaining that trust. Clients expect their lawyers to protect their data with the utmost care and diligence. Therefore, cybersecurity is not just a matter of compliance; it’s a critical component of maintaining the integrity of the legal profession and ensuring clients’ peace of mind. Legal professionals must continuously invest in cybersecurity resources, education, and training to uphold their ethical responsibilities and deliver on their commitment to clients.
Don’t stop here; you can continue your exploration by following this link for more details: Summary of the HIPAA Security Rule | HHS.gov
Cyberattacks have become more sophisticated, targeting law firms as they house valuable information, including confidential client data, financial records, and sensitive case details. The consequences of a breach can be severe, leading to reputational damage, financial losses, legal repercussions, and the loss of client trust. Therefore, cybersecurity is not just an option but a necessity in the modern legal landscape.
“In today’s digital age, law firms must prioritize cybersecurity to protect their clients, reputation, and sensitive information. Cyberattacks have evolved, posing significant threats. Implementing robust cybersecurity measures is no longer a choice but a vital obligation in the legal profession to safeguard against data breaches and their dire consequences.”
For a comprehensive look at this subject, we invite you to read more on this dedicated page: What is Cybersecurity? Everything You Need to Know | TechTarget
Law firms often store vast amounts of sensitive information, making them attractive targets for cybercriminals seeking to steal or ransom confidential data.
“Given that law firms typically house vast amounts of sensitive information, they have become prime targets for cybercriminals looking to exploit or ransom confidential data. This growing threat underscores the importance of robust cybersecurity measures within the legal profession.”
Explore this link for a more extensive examination of the topic: Healthcare Data Breaches: Insights and Implications – PMC

Cybercriminals use deceptive emails and messages to trick employees into revealing sensitive information or installing malware.
Cybercriminals employ a variety of tactics to exploit vulnerabilities, with deceptive emails and messages being a common method. These phishing attacks aim to deceive employees into divulging sensitive information or unwittingly downloading malware, posing significant threats to organizations’ cybersecurity. It’s crucial for businesses to educate their staff about these risks and implement robust security measures to mitigate such threats effectively.
If you’d like to dive deeper into this subject, there’s more to discover on this page: Healthcare Data Breaches: Insights and Implications – PMC

Malicious software can encrypt a firm’s data, rendering it inaccessible until a ransom is paid.
This type of malicious software, known as ransomware, poses a significant cybersecurity threat to organizations. When ransomware infiltrates a company’s systems, it can encrypt essential data, making it impossible for employees to access crucial files and information. Attackers then demand a ransom payment in exchange for the decryption key, essentially holding the company’s data hostage. This not only disrupts business operations but also raises ethical and legal dilemmas for organizations dealing with cybercriminals. To combat this threat, businesses must invest in robust cybersecurity measures, employee training, and disaster recovery plans to minimize the impact of potential ransomware attacks.
You can also read more about this here: Phishing Quiz | Federal Trade Commission
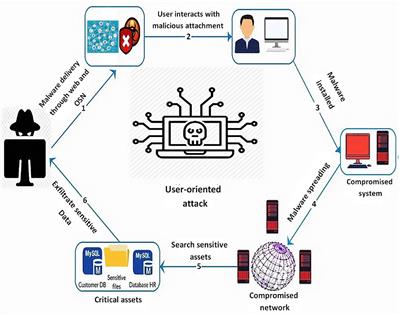
Sometimes, data breaches occur due to the actions of current or former employees with access to sensitive information.
Data breaches can be particularly concerning when they result from the actions of individuals who are supposed to safeguard sensitive data. To prevent such incidents, it’s crucial for organizations to implement robust security protocols and regularly review and update their access controls. Additionally, employee training and awareness programs can help instill a culture of data security within the organization, reducing the risk of insider threats.
Looking for more insights? You’ll find them right here in our extended coverage: Protecting Personal Information: A Guide for Business | Federal …

Educate all staff members about cybersecurity risks and best practices, including recognizing phishing attempts and avoiding suspicious links or downloads.
Creating a cybersecurity-conscious workforce is essential in today’s digital landscape. By providing comprehensive training and guidance, organizations can empower employees to become the first line of defense against cyber threats. Training should cover a wide range of topics, including:
Phishing Awareness: Teach employees how to identify phishing emails and other social engineering attacks. They should know how to spot suspicious email addresses, subject lines, and content.
Safe Browsing: Emphasize the importance of only visiting trusted websites and avoiding clicking on unknown links or downloading files from unverified sources.
Password Best Practices: Encourage the use of strong, unique passwords for each account and provide guidance on creating and managing passwords securely.
Two-Factor Authentication (2FA): Promote the use of 2FA wherever possible to add an extra layer of security to accounts.
Device Security: Train employees on securing their devices, including smartphones, laptops, and tablets, with features like screen locks and encryption.
Data Handling: Establish protocols for handling sensitive data, both online and offline, and educate employees on these procedures.
Incident Reporting: Encourage a culture of reporting security incidents promptly. Ensure that employees know how to report any suspicious activity or breaches.
Regular Updates: Stress the importance of keeping software, applications, and devices up to date with the latest security patches and updates.
Remote Work Security: Provide guidelines for secure remote work, including the use of virtual private networks (VPNs) and secure Wi-Fi connections.
Social Media Awareness: Teach employees about the risks associated with oversharing on social media and the potential for social engineering attacks based on personal information.
Remember that cybersecurity is an ongoing effort, and regular training and awareness programs should be part of your organization’s strategy to protect against evolving threats.
Should you desire more in-depth information, it’s available for your perusal on this page: Chapter 6 — Information Security, from Safeguarding Your …

Implement multi-factor authentication to ensure that only authorized individuals can access sensitive data.
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification before granting access. This typically includes something they know (like a password), something they have (like a mobile device), and something they are (like a fingerprint or facial recognition). By implementing MFA, organizations can significantly enhance their cybersecurity posture and protect against unauthorized access and data breaches.
You can also read more about this here: Protecting Information with Cybersecurity – PMC

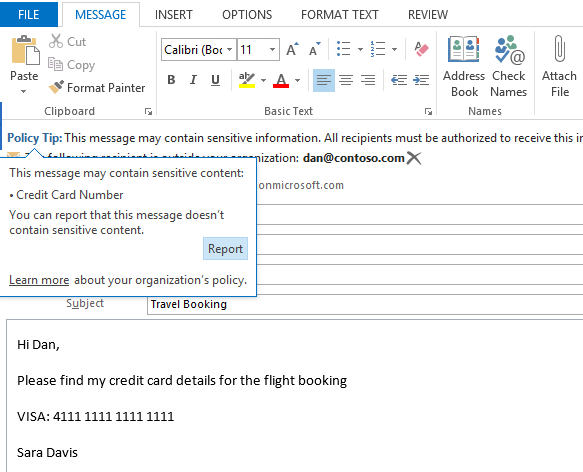
Encrypt emails and other forms of communication to protect client confidentiality.
Encrypting emails and communications is a fundamental aspect of safeguarding sensitive information in today’s digital age. By employing encryption techniques, businesses and professionals can ensure that confidential client data remains private and secure. This not only builds trust with clients but also helps organizations comply with data protection regulations and maintain the integrity of their operations. Encrypting communications is a proactive step towards a more secure and responsible business environment.
For a comprehensive look at this subject, we invite you to read more on this dedicated page: Gramm-Leach-Bliley Act | Federal Trade Commission

Regularly back up data and develop a recovery plan to ensure minimal disruption in the event of a cyberattack.
Certainly! Here’s an extended idea:
“In the digital age, law firms handle an immense amount of sensitive data, from confidential client information to legal case details. Protecting this data is not just a matter of compliance but a fundamental ethical obligation. One crucial aspect of cybersecurity in law is the need for regular data backups and the development of a comprehensive recovery plan. By diligently backing up data and creating a well-thought-out recovery strategy, law firms can ensure minimal disruption and data loss in the event of a cyberattack. This proactive approach not only safeguards client information but also upholds the integrity and trustworthiness of legal practice in an increasingly interconnected world.”
Additionally, you can find further information on this topic by visiting this page: Business Backup & Recovery Software Solution
Keep software and systems up to date to patch vulnerabilities that cybercriminals may exploit.
Regularly updating your software and systems is not just a best practice; it’s a fundamental step in safeguarding your digital assets. Outdated software can contain vulnerabilities that cybercriminals are all too eager to exploit. By staying current with updates and patches, you create a robust defense against potential security breaches. Remember, a proactive approach to cybersecurity is your best line of defense in an ever-evolving digital landscape.
Looking for more insights? You’ll find them right here in our extended coverage: Safeguarding Taxpayer Data

Develop a detailed incident response plan to swiftly and effectively address any security breaches.
Creating a comprehensive incident response plan is essential to minimize the potential damage of security breaches. Such a plan should outline specific steps to detect, contain, and mitigate security incidents swiftly. It should also specify roles and responsibilities, communication procedures, and strategies for minimizing downtime and data loss. By having a well-prepared incident response plan in place, an organization can significantly reduce the impact of security breaches, protect sensitive data, and maintain the trust of customers and stakeholders.
Looking for more insights? You’ll find them right here in our extended coverage: Protecting Personal Information: A Guide for Business | Federal …
Legal tech solutions, including advanced encryption tools, secure cloud storage, and AI-driven threat detection, have become essential for law firms. These technologies help automate security measures and provide real-time monitoring to detect and respond to threats.
In the ever-evolving landscape of cybersecurity, legal tech solutions have emerged as indispensable allies for law firms. These innovative tools offer a multifaceted approach to fortifying digital defenses and ensuring the safety of sensitive legal information.
Advanced encryption tools stand as the first line of defense, transforming sensitive data into virtually uncrackable code. This ensures that even if unauthorized access occurs, the data remains unintelligible and protected. Secure cloud storage solutions provide a secure repository for vast volumes of legal documents and records. This allows law firms to access critical information remotely while maintaining rigorous security protocols.
AI-driven threat detection systems are another key component of modern cybersecurity. Leveraging the power of artificial intelligence, these systems continuously analyze network traffic, identifying anomalies and potential threats in real-time. This proactive approach enables swift response and mitigation of cyberattacks, minimizing damage and downtime.
Moreover, legal tech solutions not only bolster cybersecurity but also enhance overall operational efficiency. By automating security measures and monitoring, law firms can allocate more time and resources to their core legal work, serving clients effectively and efficiently.
In the digital age, the integration of these cutting-edge technologies is imperative, ensuring that law firms not only protect their own interests but also uphold their commitment to safeguarding the confidential information entrusted to them by clients.
Looking for more insights? You’ll find them right here in our extended coverage: Healthcare Data Breaches: Insights and Implications – PMC

Maintaining client trust is paramount in the legal profession. Ethical obligations require lawyers to protect client information diligently. Failure to do so not only risks regulatory penalties but also legal malpractice claims.
“In the legal realm, trust is the foundation of attorney-client relationships. Legal practitioners must adhere to stringent ethical standards, ensuring the confidentiality and security of client information. Falling short not only exposes lawyers to regulatory and legal repercussions but, more importantly, erodes the trust that forms the bedrock of the legal profession.”
Explore this link for a more extensive examination of the topic: Cybersecurity Solutions for Legal Services | Attorney-Client Data …

Conclusion
Cybersecurity in law is not an option but an imperative. As technology continues to shape the legal landscape, law firms must remain vigilant in protecting sensitive data and client information. By implementing robust cybersecurity practices and leveraging cutting-edge legal tech solutions, legal professionals can uphold their ethical obligations and safeguard their clients’ trust in an increasingly digital world.
“In today’s digital age, cybersecurity in the legal sector isn’t merely an option; it’s an imperative. As technology continues to reshape the legal landscape, law firms must remain unwavering in their commitment to safeguarding sensitive data and client information. Through the adoption of robust cybersecurity practices and the utilization of cutting-edge legal tech solutions, legal professionals can not only fulfill their ethical obligations but also fortify their clients’ trust in an ever-evolving digital world.”
Explore this link for a more extensive examination of the topic: Healthcare Data Breaches: Insights and Implications – PMC
More links
Don’t stop here; you can continue your exploration by following this link for more details: Summary of the HIPAA Security Rule | HHS.gov
